Microsoft Local Administrator Password Solution (LAPS) is a free solution that provides a secure way to manage local administrator passwords on Windows computers. LAPS works by randomly generating a complex password for the local administrator account on each computer and storing it securely in Active Directory/. The password is then periodically changed and updated, helping to prevent attackers from gaining access to the local administrator account and compromising the computer or network. LAPS is a simple and effective way to improve the security of local administrator accounts across an organization's network.
Windows LAPS is the newer solution Microsoft has introduced to us. It's much easy to deploy and much easy to maintain the Administrative password. Windows LAPS also adds many features that aren't available in legacy Microsoft LAPS. You can use Windows LAPS to back up passwords to Azure Active Directory, encrypt passwords in Windows Server Active Directory, and store your password history.
Windows LAPS doesn't required to install any agent on the PCs like legacy Microsoft LAPS. Old day we used MECM (SCCM), GPO or Any 3rd party application to Deploy the client.
Windows LAPS Support Hybrid Azure AD Join and Azure AD join but doesn't support the Azure AD registered.
Same as Microsoft LAPS, Windows LAPS also freely available with Azure AD basic and above but you might be need to purchase Azure AD Premium plan 1 or plan 2 for conditional Access and Intune license for benefit the Windows LAPS other features.
Supported Operation systems
- Windows 11 22H2 - April
11 2023 Update
- Windows 11 21H2 - April
11 2023 Update
- Windows 10 - April 11
2023 Update
- Windows Server 2022 -
April 11 2023 Update
- Windows Server 2019 -
April 11 2023 Update
Manage DSRM Password
01. Windows LAPS with Intune & Azure Active directory02. Windows LAPS with GPO
01. Windows LAPS with Intune & Azure Active directory
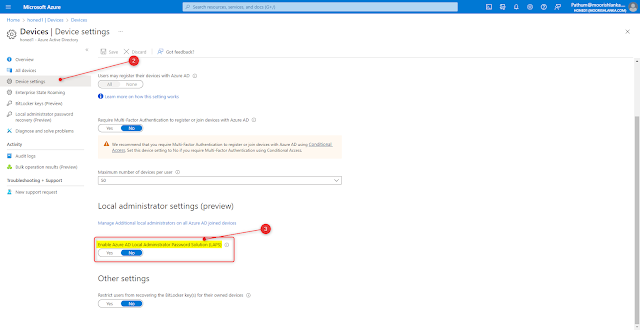
- Go to Azure Portal (Portal.Azure.com) and Azure Active directory
- Open and Devices and select Device Settings
- Enable Azure AD Local Administrator Password Solution (LAPS)
4. Go to Intune Admin Portal and open Endpoint Security
5. Select Account Protection
6. Create a new Policy
7. Select Windows 10 and later and Select Local admin password solution (LAPS)
8. Create the Policy
9. Change the configuration as Required
Enable Built-in Administrator Account
By Default Built-in Administrator Account account is disable on the AAD-Joined Devices. follow below configuration to enable the Administrator account.- In the Intune Admin portal. go to Devices.
- New Configuration Profile
- Select Windows 10 and Later
- Select Template
- Select Custom
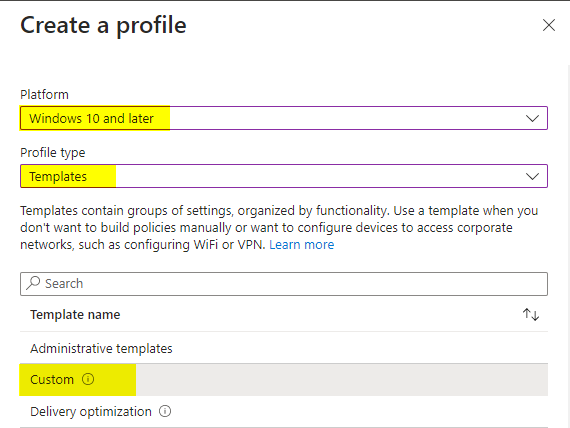
6. Provide name and Fill the configuration as below
- Name: [Any Name]
- OMA-URI: ./Device/Vendor/MSFT/Policy/Config/LocalPoliciesSecurityOptions/Accounts_EnableAdministratorAccountStatus
- Data type: Integer
- Value: 1
7. Assign the Policy
With these configuration you have successfully Deploy the Windows LAPS with Azure AD.
Create a New local account
personally I like to create a new account for deployment rather we using the built in administrator. steps are below.
- In the Intune Admin portal. go to Devices.
- New Configuration Profile
- Select Windows 10 and Later
- Select Template
- Select Custom
- Provide name and Fill the configuration as below
- Name: Create Local User Account
- OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/ABCadmin/Password
- Data type: String
- Value: mmMM12!@
7. Select Add
- Name: Add user to Local administrator group
- OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/ABCadmin/LocalUserGroup
- Data type: Integer
- Value: 2
Validate:
Retrieve the password
02.Windows LAPS with GPO
- Open the Group Policy Management
- Create a new Computer Policy
- Right click and Edit then Navigate to Computer Configuration > Policies > Administrative Templates > System > LAPS
4. Open Configure password backup directory Select the Manage AD. (if device are not manage on Azure AD. select Active directory)
5. Open Password Settings and enable the setting and Enable
There are other policies that you can configure.
- Enable Password backup for DSRM account - This will backup the DSRM administrator account to Active directory
- Configure size of encrypted password history - specified number of older passwords will be stored in Active Directory.
- Enable Password encryption - managed password is encrypted before being sent to Active Directory. Password has to backup to Active directory and Domain functional level has to be 2016 and above.
- Configure authorized password decryptors - specific user or group who is authorized to decrypt encrypted passwords.
- Name of Administrator account to manage - specifies a custom Administrator account name to manage the password for. Built in administrator account doesn't not need this policy. auto-detected by well-known SID and does not depend on the administrator account name.
Troubleshoot
You can troubleshoot using event viewer.
Event Viewer > Application and services logs > Microsoft > Windows > LAPS
.png)


























0 comments:
Post a Comment