System-preferred multifactor authentication (MFA) is a security feature that prompts users to sign in using the most secure method they have registered. This can help to improve sign-in security and discourage the use of less secure methods, such as SMS.
For example, if a user has registered both SMS and Microsoft Authenticator push notifications as MFA methods, system-preferred MFA will prompt them to sign in using the push notification method. The user can still choose to sign in using another method, but they will be first prompted to try the most secure method they have registered.
If you are an administrator, I encourage you to consider enabling system-preferred MFA in your organization. This is a simple way to improve the security of your sign-in process and protect your users' data.
Enable system-preferred MFA in the Entra ID portal
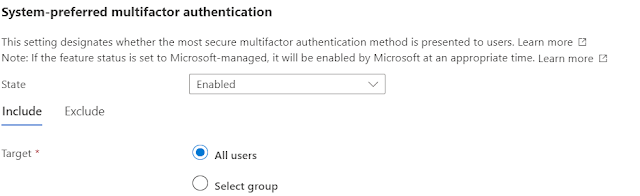
In the Azure portal, click Security > Authentication methods > Settings.
For System-preferred multifactor authentication, choose whether to explicitly enable or disable the feature, and include or exclude any users. Excluded groups take precedence over include groups.
How does system-preferred MFA determine the most secure method?
When a user signs in, the authentication process checks which authentication methods are registered for the user. The user is then prompted to sign in with the most secure method according to the following order. The order of authentication methods is dynamic, meaning it is updated as the security landscape
changes and as better authentication methods emerge.
Temporary Access Pass
A one-time passcode that is generated and sent to the user via email or SMS.
- FIDO2 security key
A physical security key that the user inserts into their computer or mobile device to authenticate.
- Microsoft Authenticator push notifications
A notification that is sent to the user's Microsoft Authenticator app. The user can then approve the sign-in attempt from their app.
- Time-based one-time password (TOTP)
A code that is generated by the user's phone or other device. The code changes every few seconds, making it difficult for attackers to guess.
- Telephony
A phone call or text message that is sent to the user. The user then enters a code from the call or text message to authenticate.
- Certificate-based authentication
A digital certificate that is installed on the user's computer or mobile device. The certificate is used to authenticate the user when they sign in.
.png)

.png)










0 comments:
Post a Comment